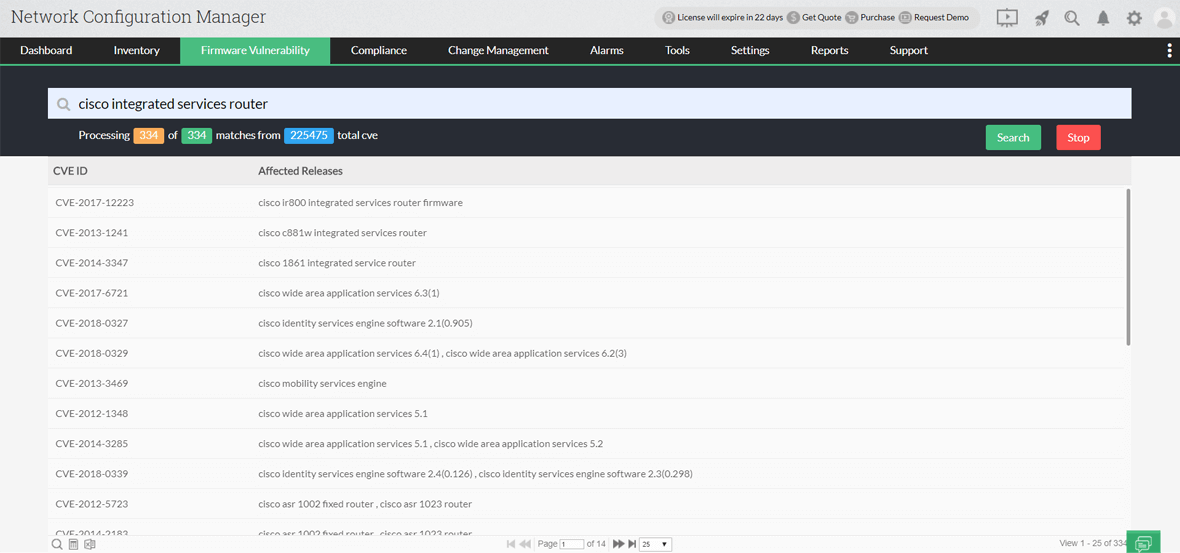
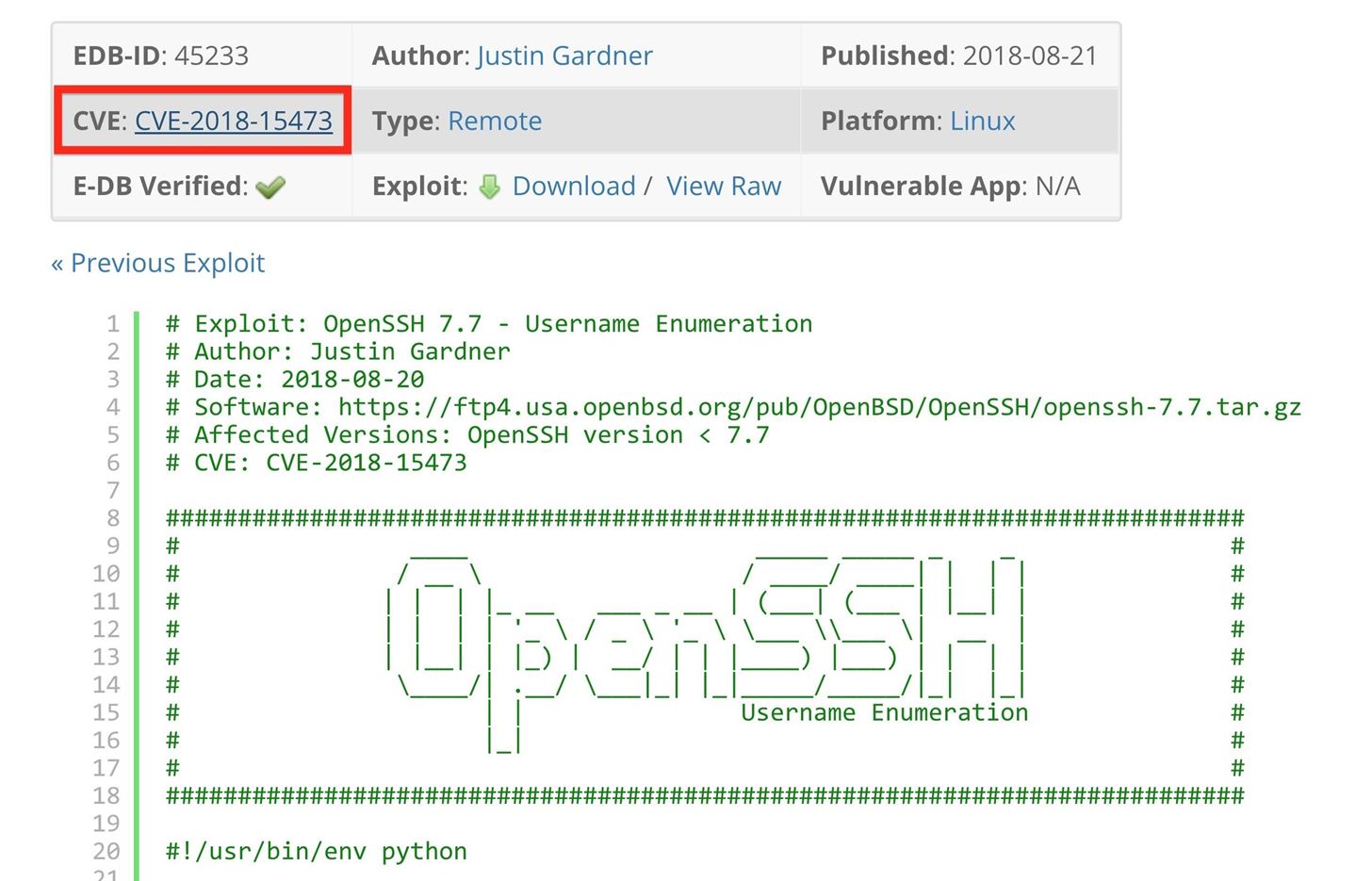
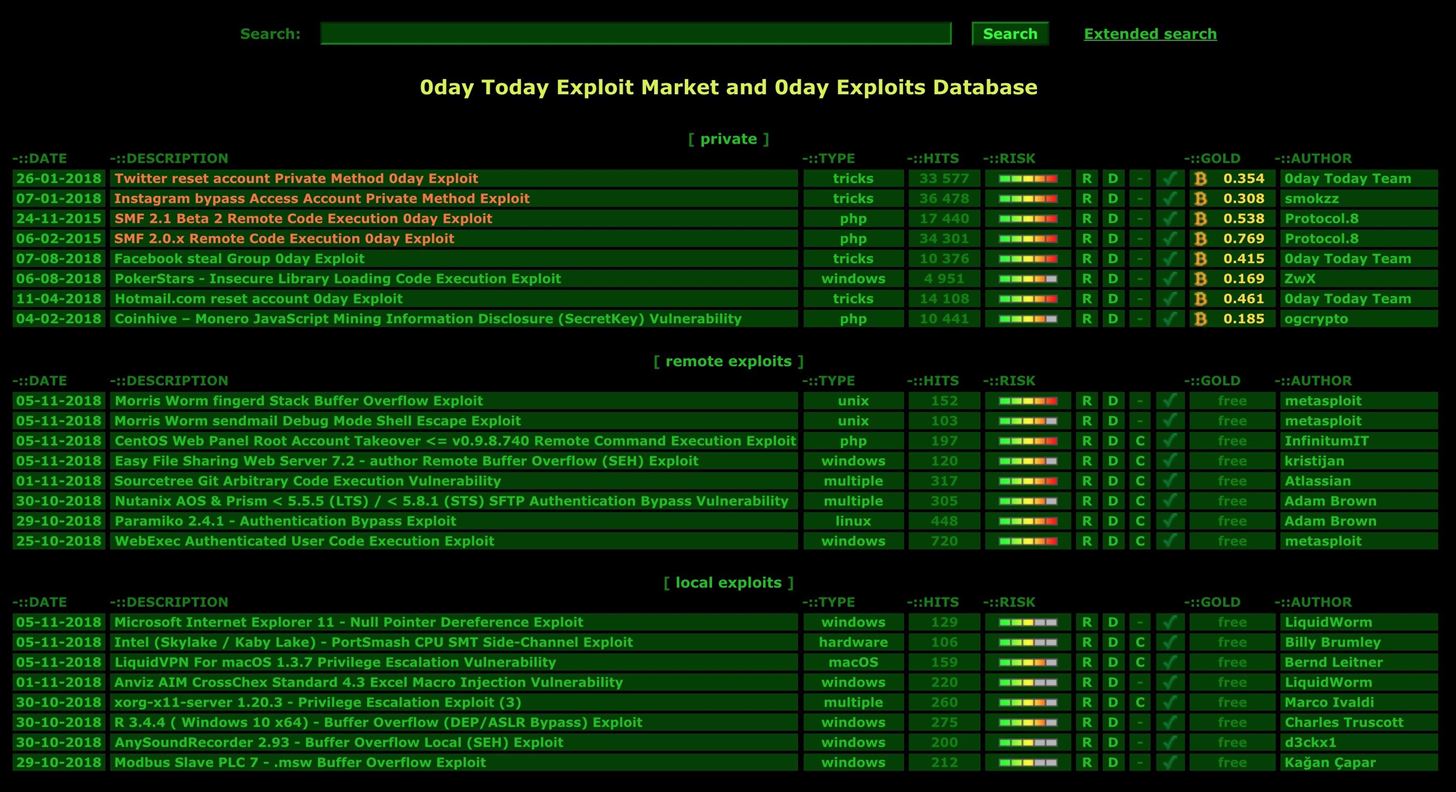
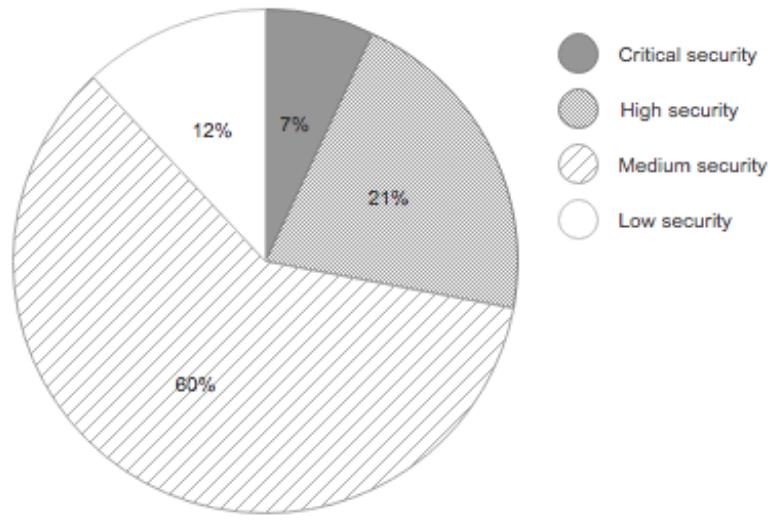
![Jinwook Kim on Twitter: "Huawei dg8045 - Authentication Bypass The default password of this router is the last 8 characters of the device's serial number [PoC] GET /api/system/deviceinfo HTTP/1.1 .. SerialNumber":"21530369847SK9252081" hxxps://www ... Jinwook Kim on Twitter: "Huawei dg8045 - Authentication Bypass The default password of this router is the last 8 characters of the device's serial number [PoC] GET /api/system/deviceinfo HTTP/1.1 .. SerialNumber":"21530369847SK9252081" hxxps://www ...](https://pbs.twimg.com/media/E4tXRC8UcAAkhDQ.png:large)
Jinwook Kim on Twitter: "Huawei dg8045 - Authentication Bypass The default password of this router is the last 8 characters of the device's serial number [PoC] GET /api/system/deviceinfo HTTP/1.1 .. SerialNumber":"21530369847SK9252081" hxxps://www ...

Bad Packets by Okta on Twitter: "⚠️ WARNING ⚠️ Unauthenticated Remote DNS Change Exploit Detected Target: D-Link routers (https://t.co/TmYBAAR1T7) Source IP: 35.240.128.42 (AS15169) 🇺🇸 Rogue DNS server: 144.217.191.145 (AS16276) 🇨🇦 https://t.co ...